A question I am often asked is if a particular site is safe and secure to play on. Many times I hear “it has a lock on the page so it must be safe.” “The best way for gaming applications to become more secure is for the user to press the operators to improve security of their sites.” Now, while there are no guarantees, there are some items you can look for that may give you a clearer picture of a site’s overall security posture. In this article we will look at tools and basic techniques you can use to examine a site’s security utilizing a passive approach.
This article may be slightly more technical then the previous ones I have written for pokerfuse, although I have tried not to get too deep into the weeds. Even if you do not actually perform any of the outlined tests, hopefully you will be better informed on what can be done.
Passive and Active Security Testing
“Passive” is the keyword here. In security testing, you can utilize two different techniques: active and passive. The primary difference is that in active testing you are creating traffic and sending it to the server. An example of active testing would be running an application vulnerability scanner against a web-based gaming application.
Active testing is intrusive and I do not recommend performing this level of testing unless you have specific permission from the game provider as it may be considered illegal in some jurisdictions. When we are contracted by game providers to perform testing of an application, active testing is a large percentage of the work we do and we always have signed rules of engagement before proceeding.
Passive testing on the other hand only involves listening to the normal traffic that is being transmitted between the game client and the game server. By doing this you can learn some information on how well the site is secured. By performing only passive testing you most likely will not uncover any critical vulnerabilities, such as SQL injection or application logic flaws. But if you do notice some of the issues I will illustrate in this article, it may lead you to question how well other controls are implemented and if the site is secure.
The rise of browser-based clients.
In this article we are going to cover how you can examine sites that offer gaming via a web-based client. In the past few months I have seen more customers developing this type of platform in addition to the typical PokerStars and Full Tilt type applications where you download and install the client software to your computer.
When you offer gaming through a web browser it does introduce some additional security concerns that need to be taken into account. The two primary types of tools that we are going to cover in this article are:
- Web Proxy
- Network Sniffer
All of the tools listed in this article are free and run on both Windows and Linux systems.
Tapping in to web traffic with ZAP and Burp
A web proxy is a tool that we can use to examine HTTP traffic between the web client and the web server. We can even use it to intercept and modify data, although this would not be considered passive.
Typically the web proxy will be installed on your local system and your web browser will be configured to send traffic to the proxy, which will then send it to the destination. There are many different web proxies that can be used. Two that I like are Zed Attack Proxy and Burp Proxy.
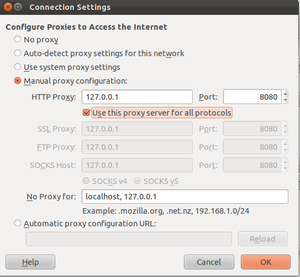 In addition to their proxy features both also perform passive vulnerability detection. In other words, by simply configuring your browser to use the proxy and playing on the site as normal, vulnerabilities may be detected. To configure your browser to use a proxy you must modify the network settings. The figure to the right shows how to do this for Firefox.
In addition to their proxy features both also perform passive vulnerability detection. In other words, by simply configuring your browser to use the proxy and playing on the site as normal, vulnerabilities may be detected. To configure your browser to use a proxy you must modify the network settings. The figure to the right shows how to do this for Firefox.
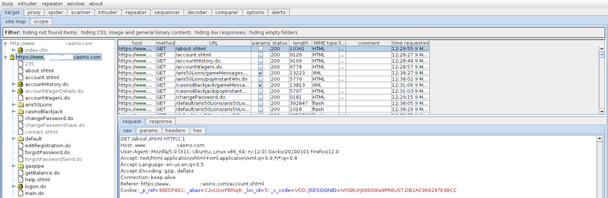
You can also used a plugin such as FoxyProxy, which is my preference as it allows you to switch more easily between different proxy settings. Once you do this, fire up your favorite proxy and browse to the site you want to examine. Just by browsing and playing on the game site all traffic will be captured and can be examined at a later time. A mapping of the application structure can also be viewed.
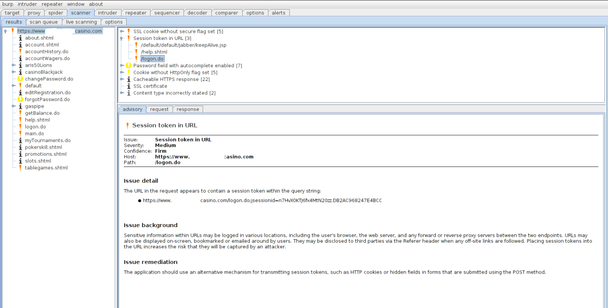
Even more important, potential vulnerabilities will be detected passively just by examining the traffic log on the proxy. This can be seen in the figure below on an application I looked at (the URL is modified for the operator’s privacy).
As you can see, several issues were noted, and while none would lead to a direct compromise of the site, you can draw some conclusions about other areas. If the site is not securing the cookies correctly or following best practices with the session token, what else could they be doing wrong? This was all discovered in less than five minutes.
Other items you can look at to get an idea of how the application is handling security are password requirements. Do they allow weak passwords or are complex passwords required? What about account lockout and session termination? These are items that secure applications will have in place.
Network Sniffing with Wireshark
In addition to a web proxy, a network sniffer can also be used to passively examine the application. A network sniffer captures all traffic (not just HTTP) between your system and the destination. The most popular packet capture tool is Wireshark. All you need to do is run Wireshark on your system and visit the site you want to examine.
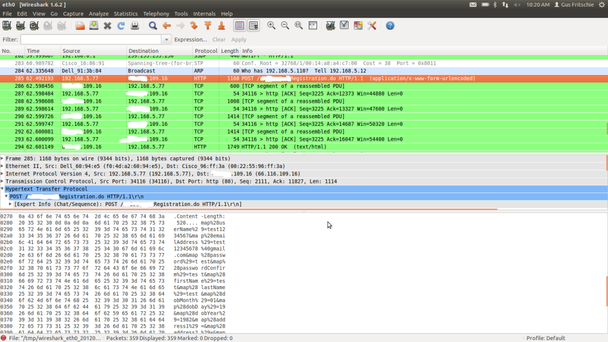
This is also a good tool to use when examining traditional gaming software where the client is installed on your computer. Do note, this tool will capture a lot of traffic and you will need to filter it for the information that you are interested in. In the figure below we use the tool to capture traffic during the registration process for a gaming application. As you can see, the username and password are being passed in clear-text, something you should not see in a secure application.
While none of these basic steps outlined above replace the need for an independent detailed application vulnerability assessment, they can be performed relatively quickly and easily by an average user. The best way for gaming applications to become more secure is for the user to press the operators to improve security of their sites. If you notice something that looks insecure, ask the operator about it and insist that it gets fixed. Only by working together can iGaming be made safe and secure.