


“At the latest security conference I attended … over half of the talks focused either on how to break mobile devices or how to secure them.” The future is here and it is mobile. I see it first-hand as more and more people want to bring and connect their mobile devices to corporate networks, and as my team attempts to manage them in a secure fashion.
We are also starting to see this in online poker, though not in the United States (for obvious reasons). It is clear why this is exciting. You have to look no further than Apple and its rise, mostly due to the popularity of the iPhone and iPad. There is an appeal of being able to play a “sit-and-go” or a few hands of a cash game while on the go, such as waiting in a doctor’s lobby or traveling on the train.
But with this convenience comes some risk. Being based in the United States, I have not performed any actual testing on the mobile poker games being offered by PokerStars and others (yes, I could most likely circumvent these restrictions, but that is a story for another article). Due to the inability to actually perform testing, this article will cover at a high level some of the security risks specific to mobile devices and what developers and players of games need to know.
Growth of Mobile
Part of my job as an information security professional is to attend industry conferences. Two years ago, there were not many talks on mobile security. At the latest security conference I attended in February, I would estimate that over half of the talks focused either on how to break mobile devices or how to secure them. This illustrates that more people in the security community are taking notice of mobile devices, the vulnerabilities they introduce, and the valuable data they contain.
And it is not just security-specific conferences: I was at the iGaming North America conference earlier this month, and one of the “takeaways” I came away with from several panel discussions was that mobile gaming will be big. Now, whenever something gains attention, you will see people looking to take advantage of it. One method to do this is to compromise the security of mobile applications.
Threats to Mobile Clients
When it comes to application security, the most important factor is secure code. Code is more difficult to secure on mobile devices for a variety of reasons: Technology, diverse platforms, privacy concerns, and experience, to name a few. As we have seen recently with the {n:security-issue-exposed-lock-pokers-casino:Lock Poker casino password issue}, some developers can’t seem to write secure code in traditional environments. 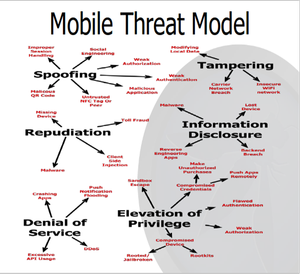 I am scared to think what might happen in mobile environments.
I am scared to think what might happen in mobile environments.
You can’t just take the code for a non-mobile, online poker game and move it over to a mobile platform; numerous changes are going to be required. As discussed earlier, one reason is that mobile platforms vary greatly from iOS to Android, for example. Also, how people use applications and their usage patterns are different on mobile devices. Other factors besides just the poker application need to be considered, such as remote Web services, platform integration, and device-specific security issues. The threats are also different (illustrated in the figure to the side; click for large).
Securing a Mobile Application: Best Practices for Developers
With these threats, there is the need for specific mobile security controls. Luckily for us, we have the Open Web Application Security Project (OWASP). OWASP has been around for some time and has been the standard when it comes to application security. With the emergence of mobile technologies, OWASP has recently added the Mobile Security Project, headed by Jack Mannino, to their list of contributions. As part of the project, they have documented the top ten mobile security controls. They are listed below, but this information and more can be found on their web site.
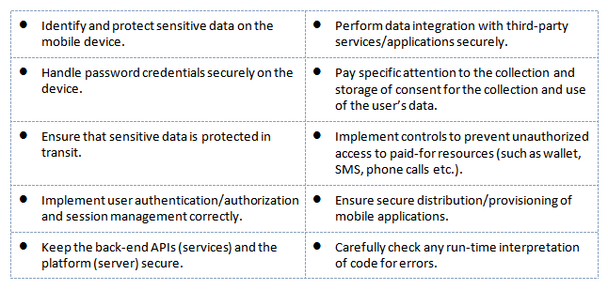
If developers follow these controls and design their applications in a secure manner, it will make those who are attempting to compromise these devices have to work harder.
Along with developers, it is important that regulatory bodies and the companies they hire to test controls verify that the controls are implemented correctly. The method to examine mobile applications is similar in some aspects to traditional Web application testing, but different in others.
At a high level, the following tests must be performed, both from dynamic and static perspectives, to verify that all security controls are in place. Dynamically, the tester should debug the poker application either on the device or in an emulator. Ingress and egress network traffic should also be analyzed including remote services (i.e., HTTP/SOAP). Statically, it is best if the source code is provided so that it can be examined using an automated code analysis tool and manually examined. Otherwise, a static binary analysis should be performed. Reverse engineering and disassembly are also techniques that security testers should utilize. As you might imagine, sophisticated testing is not a trivial task and requires testers with the right skill sets.
Tips for Poker Players on Mobile Devices
From a user perspective (besides following some of the practices I outline in my previous article), if you are going to play poker from a mobile device, the most important item is not to ‘jail-break’ it. Yes, it is neat to have access to additional features and applications, but by jail-breaking the device, you introduce additional security risks.
Mobile antivirus is another solution that while it will not solve all problems is recommended to have installed. It is also important to only install software from trusted markets (i.e. Apple, Amazon, Google Play). When installing anything (even from trusted sources), pay close attention to the permissions an application requests, as well as the size of the install base and the ratings.
In case you lose your device, make sure you have a reasonable screen lock timer, use a strong password (not 1234), and have the ability to remotely wipe the device. When done playing that tournament on your iPad make sure to sign-out of the poker application as many mobile applications are very generous with their session expirations.
Hopefully, this article has given you some insight into some of the risks and security controls related to mobile applications. In early April, I will be attending the OWASP AppSec DC 2012 conference. Several talks on mobile application security are scheduled and I will be sure to provide feedback from the conference in a future article.

