When most people think about computer security, they often assume that if they have antivirus software, they are safe. Now, of course, having antivirus software installed with updated virus signatures is a required first step, Passwords are the first that come to mind—there is no need for a complex attack if your password is poker.’ This advice goes for all accounts, not just your poker accounts. E-mail accounts in particular must have strong passwords—just ask Daniel Negreanu.
but when your computer is used to play a game where hundreds to thousands of dollars are at stake, more protection is needed.
There have been several reported cases where players have been cheated because their opponents could see their hole cards or other security exposures. While there are sophisticated attacks (such as the man-in-the-middle SSL misconfiguration vulnerability that affected Ultimate Bet Poker [AP]) that could be used to obtain this information, it is more common that a player will be tricked into installing some form of malicious software on their system.
This is not an attack vector that is unique to the online poker industry. Several high-profile attacks in both the government and private sectors have used this method successfully. The RSA (the company that makes those 2-factor authentication tokens that more sites are making available) security breach is a great example.
In this case, an employee was tricked into opening a document that had malicious code, which installed a backdoor that the attacker then used to gain access to RSA’s internal network and eventually portions of RSA’s security algorithm. Now, if an organization whose primary mission is information security can be exploited in this manner, it is likely that the vast majority of the online poker population could also be successfully targeted.
As discussed, while there are several different attack vectors that could be used to gain unauthorized access to a player’s system, two of the most common are old-fashioned social engineering and phishing attacks.
Social engineering is the process of deceiving people into giving away access or confidential information. This topic will not be discussed in this article; rather, we will focus on defenses against client-side attacks such as phishing. There are two primary categories of phishing: general and spear.
- Phishing – E-mails that typically contain a link to a counterfeit Web site and are designed to look like an authentic login page. They will actually capture personal data for cyber criminals, who will use the data to commit financial fraud.
- Spear Phishing – Targets are identified in advance and the e-mails that attempt to trick them into handing over personal data can be highly specific. They might claim to come from a friend or colleague, or seek to exploit the target’s known interests.
Of the two, spear phishing attacks are much more dangerous. I can imagine several scenarios that could be used against well-known and successful players in order to launch a successful attack.
There are several obvious defenses that players can use to better protect themselves from these types of attacks. Passwords are the first that come to mind—there is no need for a complex attack if your password is “poker.” This advice goes for all accounts, not just your poker accounts. I believe that the most important protection mechanism you can use is a dedicated system on which you only play online poker.
E-mail accounts in particular must have strong passwords—just ask Daniel Negreanu. A separate poker-specific e-mail address is also a good idea.
It is best to have separate passwords for all accounts and ensure that they are complex (I recommend at least 14 alphanumeric characters including special characters). If the option is available to use some sort of multi-factor authentication token, take advantage of it.
Another step is to keep your system up to date will all security patches, not just operating system patches but also third-party updates from companies like Adobe and Java. Attackers’ phishing exercises are usually successful because their victims are running outdated software, which makes their computers easier to exploit.
I believe that the most important protection mechanism you can use is a dedicated system on which you only play online poker. Don’t surf the Web, answer e-mails, use instant messaging, or run anything else on this system. A dedicated system should not only increase your win rate (since you will not be distracted), but it will help you avoid certain types of client-side attacks such as phishing and cross-site scripting (XSS) attacks. During our research last summer, we found numerous sites (both online poker companies and supporting sites) that were vulnerable to client-side XSS attacks. From OWASP.org, XSS is defined as follows:
Cross-Site Scripting attacks are a type of injection problem, in which malicious scripts are injected into the otherwise benign and trusted web sites. Cross-site scripting (XSS) attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user in the output it generates without validating or encoding it.
An attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by your browser and used with that site. These scripts can even rewrite the content of the HTML page.
As you can see, there are a number of possible attacks that could occur. Imagine that you were logged in to a site playing poker, you visited a site that was vulnerable to XSS, and the payload captured your cookies and sent them to the attacker. The attacker could then use these cookies to potentially log in to the poker site on which you were playing. The possibilities are unlimited and this is why I advise not to do anything else on your poker system except play poker.
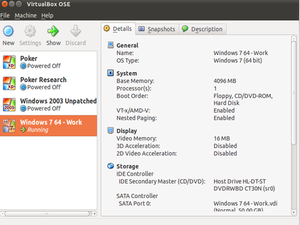
Now, it may be costly or just not practical to use two separate computers. If this is the case, do what I do: use virtualization. With the technologies available today such as VMware or VirtualBox, is easy to have a separate virtual machine dedicated for your poker playing. For my computer setup, I use Ubuntu Linux as my host operating system and VirtualBox for my guest operating systems (see figure below).
This setup allows me to have a dedicated system for poker playing and others for research and work. Now, you will need a system with a substantial amount of memory or you may run into performance issues, but with memory so inexpensive, this should not be a problem in most cases. There are plenty of articles on the Internet about installing and using virtualization, so they should point you in the right direction if you are not familiar with this technology. If you have any questions, please let me know and I will consider writing an article on installing a virtualized system geared toward poker players.
If you follow the suggestions in this article, you will hopefully decrease the risk of your system and poker account becoming compromised. In my next article, I will look at the increase of online poker applications being offered on mobile devices and the security concerns in that environment.