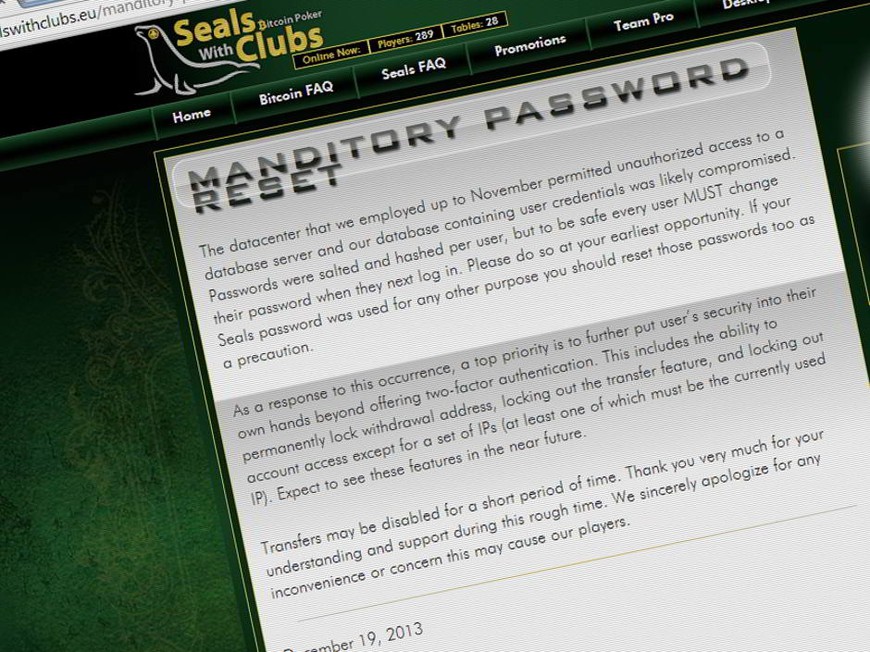

- Bitcoin only site SealsWithClubs (SwC) has warned players that they must reset their passwords after a datacenter permitted unauthorized access to the database containing users details.
- Over 42,000 hashed passwords believed to belong to SealsWithClubs users were posted on a public forum where world-class professionals were offered money to help uncover original passwords from the hashes.
- Seals with Clubs chose the cryptographic hash is described by experts as a “poor” choice “ill-suited” for passwords due to the “minimal computing resources” required to crack the algorithm.
The article has been updated to include comments from site representative Bryan Micon.
Bitcoin-only poker room SealsWithClubs (SwC) has warned players that they must reset their passwords after a datacenter permitted unauthorized access to the database containing users’ details.
“Passwords were salted and hashed per user, but to be safe every user MUST change their password when they next log in,” the statement explains.
The issue is of particular concern as over 42,000 hashed passwords believed to belong to SealsWithClubs users were posted on a public forum where world-class professionals were offered money to help uncover original passwords from the hashes.
Tech site Ars Technica reported cracked passwords including “sealswithclubs, 88seals88, bitcoin1000000, and pokerseals” lead experts to believe that the posted hashes were representitive of passwords belonging to SealsWithClubs users.
The poster is offering $20 for every bundle of 1,000 passwords recovered. As of the time of publishing, it appears over 70% of the hashes have been converted, with one poster confirming payment for his services.
Seals with Clubs chose the cryptographic hash SHA1. For years SHA has been considered insecure for its susceptibility to collision attacks; Ars Technica describes this as a “poor” choice “ill-suited” for passwords due to the “minimal computing resources” required to crack the algorithm.
SwC suffered a different type of security problem nine months ago. Their systems were the victim of a Distributed Denial of Service (DDoS) attack, which shut the site down for two days. No player accounts were compromised at that time, and SwC announced a “new, beefier setup with all of our data intact and a sick DDoS protection layer.”
Two-factor authentication has been available since April, and the accounts of these players should not have been compromised, although passwords changes are still required.
Site representative Bryan Micon told pokerfuse:
Simply put we have upgraded the critical systems that failed. Our datacenter permitted unauthorized access and our internal security systems were unfortunately lacking. It is quite embarrassing to us. We have upgraded all parts of that internal system and fired the datacenter. A password change is needed from the user. The situation is far from ideal but Seal Team 6 (our technical team) responded swiftly and continues to monitor the inbox to help all users who may still be having issues getting back on.
Further security upgrades are promised after this latest security breach, including the ability “to permanently lock withdrawal address, locking out the transfer feature, and locking out account access except for a set of IPs” (at least one of which must be the currently used IP).” However it is unclear if the owners intend to increase the security of users’ passwords by moving to a more secure cryptographic hash.
Micon continued, “I cannot speak of specific technical terms but understand the system has been overhauled. It is not the same system as before, and as I understand it far better than what was in place last week.”
SwC also warned that money transfers may be disabled for a short time.

